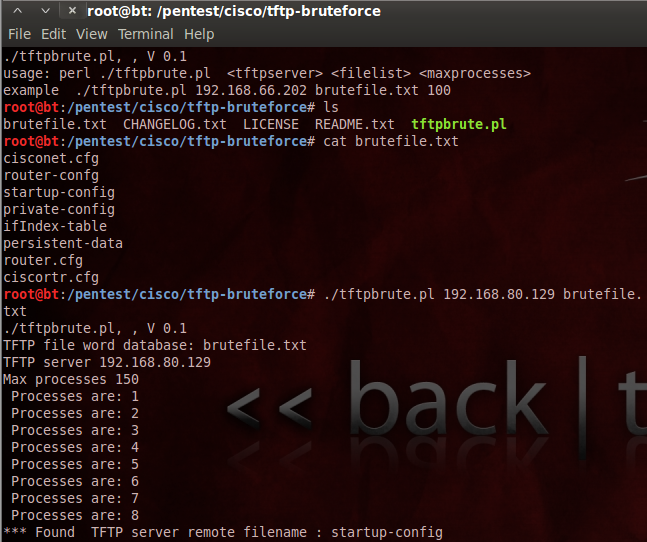
This is similar to the previous two tools, so do not expect too much, this can search for telnet passwords and SNMP community strings. It's better in one way than the previous programs: we can give a list of words for testing passwords, and it will try all of them. Unfortunately, it doesn't look for the enable password.
The usage is also very easy, but it has a couple of more options. Example:
root@bt:/pentest/cisco/cisco-auditing-tool# ./CAT -h 192.168.80.132 -w lists/community -a lists/passwords
This will scan the host at 192.168.80.132, the "lists/passwords" contains the telnet passwords and the "lists/community" the SNMP strings.